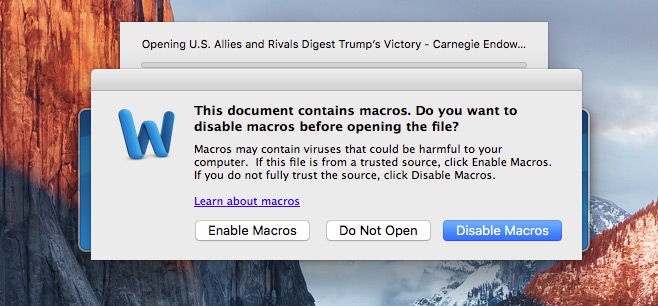
A new piece of malware that specifically targets Mac operating systems has been discovered. Found in an infected Word file, when launched on a MacOS machine, the file automatically triggers a macro which can download an encrypted payload and begin running it on the user's system.
Anyone who's been interested in technology for at least a decade is familiar with the tired maxim that Apple devices don't get viruses. Apple even used it in its old “I'm a Mac” adverts with Jason Long. They do though and as Apple devices become more commonplace, malware that targets them has followed suit.
The malware this time around was discovered in an infected Word document called “U.S. Allies and Rivals Digest Trump's Victory – Carnegie Endowment for International Peace.” A surprisingly wordy and official sounding document that seems likely to be targeting a specific group of people.
Source: Objective-see
If one of those people should have opened the document however, it would have immediately attempted to run a macro. While MacOS users would receive a warning at that point, if they were to ignore it, the malware would first check to see if the LittleSnith firewall was running. If not, it would download a payload from an infected URL, decrypt it and execute said payload.
While Ars and the security researchers it quotes don't know exactly what the payload does, the codebase that it borrows from would suggest that it would likely monitor webcams, record keystrokes, access browser histories and steal stored passwords.
Although the attack is said to not be the most sophisticated, it does show that more of the commonplace tactics for targeting Windows users are migrating over to MacOS systems too. Much like phishing attacks, Word macros utilise humans as the weak point in the security chain. Why try to break into a system manually if you can have people do it for you by opening a malicious file?
Discuss on our Facebook page, HERE.
KitGuru Says: This is why the two most important security measures you can take on any system, are to not open email attachments unless they were expected and come from a trusted source – and even then scan them first – and don't click links sent to you. Always copy and paste or check them out first.
 KitGuru KitGuru.net – Tech News | Hardware News | Hardware Reviews | IOS | Mobile | Gaming | Graphics Cards
KitGuru KitGuru.net – Tech News | Hardware News | Hardware Reviews | IOS | Mobile | Gaming | Graphics Cards