Earlier this week, a malware attack referred to as ‘ExPetr' began infecting systems in a few countries, starting off in the Ukraine before spreading to Russia and eventually the US. The tricky thing with this attack was that it had all the signs of ransomware but after doing some digging, security experts have come to the conclusion that it was a more dangerous ‘wiper' attack in disguise, meaning the attackers were there to cause damage with no intention of decrypting files.
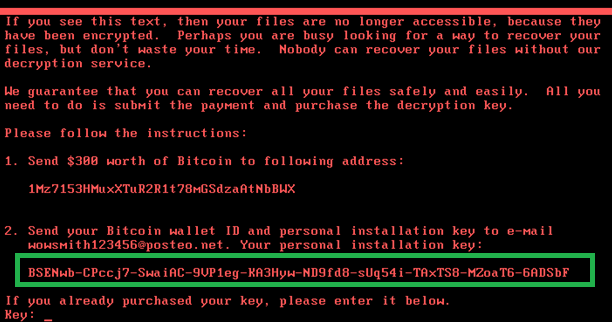
Kaspersky Labs and Matt Suiche of Comae Technologies both came to the conclusion that ‘Petya' was not ransomware after conducting their own independent investigations. While infected systems would show a splash screen asking for $300 worth of Bitcoin to be sent to a wallet in exchange for a decryption key, the payment pipeline was very poor, almost as if it was designed to fail. There is a single BTC wallet address hard coded into the malware but the instructions require sending an email with a large amount of complex strings to a single email address. Not only would it be unlikely that a novice computer user would manage to get the strings correct, but the email address provided was shut down within hours, leaving victims with no way of getting in touch with their attackers.
Image Source: Securelist/Kaspersky
As Matt Suiche points out in his post, if this attack was really supposed to generate revenue, then the group behind it went about it in the worst possible way. Beyond that, as seen in Kaspersky's investigation post, the installation ID (see above) generated on each infected system is made up of randomly generated data using the CryptGenRandom function. This randomly generated data is then encoded using the ‘BASE58' format.
This use of randomly generated data essentially means that the attacker can't extract decryption information from the ID shown to victims. Essentially meaning those infected can't decrypt their drives using the installation ID at all. This furthers the theory that the goal here was to destroy data, rather than generate revenue by holding it hostage.
KitGuru Says: This is certainly one nasty attack. The running theory right now is that it was state sponsored and built to target the Ukraine government and companies doing business with it specifically. Investigations into who is responsible are still under way.
 KitGuru KitGuru.net – Tech News | Hardware News | Hardware Reviews | IOS | Mobile | Gaming | Graphics Cards
KitGuru KitGuru.net – Tech News | Hardware News | Hardware Reviews | IOS | Mobile | Gaming | Graphics Cards