Two weeks ago, Microsoft stepped in to help distribute Intel’s Spectre and Meltdown fixes as individual vendors would have been too slow. It looks like the Redmond-based company isn’t done just yet, either, as now it’s offering a bug bounty program for anyone that identifies an attack based on the flaws.
“Speculative execution is truly a new class of vulnerabilities, and we expect that research is already underway exploring new attack methods,” said Phillip Misner principal security group manager at the Microsoft Security Response Center. “This bounty program is intended as a way to foster that research and the coordinated disclosure of vulnerabilities related to these issues.”
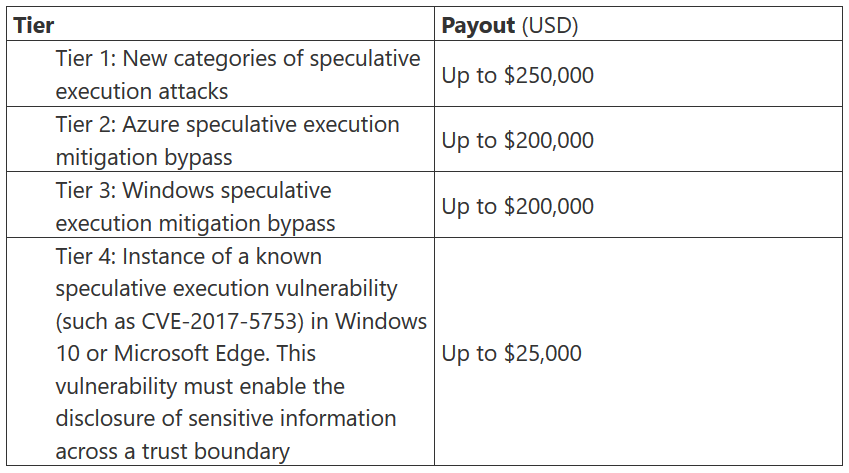
Bug hunters will have until 31st December 2018 to claim a reward up to $250,000 for finding new attack vectors and speculative execution flaws that had previously gone unaccounted for. This is the upper tier of four, with the lowest tier still offering a sizeable $25,000 for more information on already known speculative execution vulnerabilities.
“Speculative execution side channel vulnerabilities require an industry response. To that end, Microsoft will share, under the principles of coordinated vulnerability disclosure, the research disclosed to us under this program so that affected parties can collaborate on solutions to these vulnerabilities,” explains Misner.
So far, the response to such high-profile security risks has been debatably slow. Microsoft revealing the findings of its bug bounty program hopes to get things back on track, enabling companies to better prepare fixes to mitigate Spectre and Meltdown.
KitGuru Says: Microsoft’s bug bounty program has a lot of potential in quelling Spectre and Meltdown issues, and is perhaps the best effort we’ve seen towards a long-term solution for affected CPUs.
 KitGuru KitGuru.net – Tech News | Hardware News | Hardware Reviews | IOS | Mobile | Gaming | Graphics Cards
KitGuru KitGuru.net – Tech News | Hardware News | Hardware Reviews | IOS | Mobile | Gaming | Graphics Cards