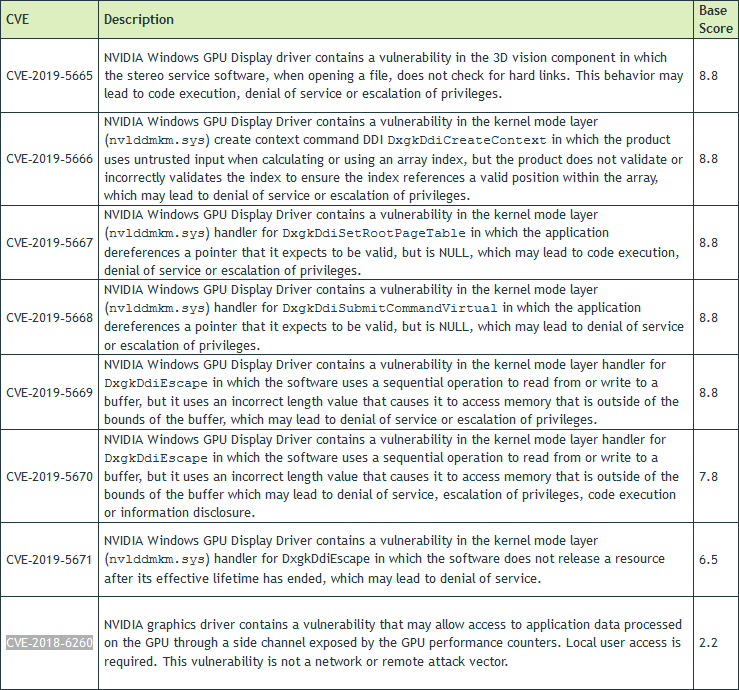
Nvidia has unleashed its first security patch of 2019, fixing eight security issues that were present in its GPU Display Driver software. It is advised that both Windows and Linux users update their systems as soon as possible; otherwise they risk possible code execution, denial of service, the dissemination of personal data and perhaps worst of all escalation of privileges.
Using the Common Vulnerability Scoring System (CVSS) v3, Nvidia revealed that five of the eight flaws received a “high” severity rating of 8.8, all impacting the NVIDIA Windows GPU Display Driver. On the lower end of the scale, the only Common Vulnerabilities and Exposures (CVE) to affect both operating systems received a rating of 2.2. Interestingly, CVE‑2018‑6260 has previously been identified as early as November, pertaining to side-channel attacks in all GPUs, including AMD.
Fortunately, the ratings were kept below the “critical” line as none of the software issues could be exploited remotely, requiring local user access. Overall, the company’s highly popular GeForce gaming series was affected, alongside the Quadro, NVS and Tesla lines.
Those that are still running out-dated Nvidia graphics drivers are leaving their system vulnerable to a multitude of ways an attacker can gain control. While code execution and denial of service could result in systems being unusable, escalation of privileges is the scariest outcome given that attackers can potentially do anything malicious without admin restrictions.
Nvidia GeForce users on Windows should ensure that they have installed the latest driver, version 419.17. Professional cards on Windows and Linux users across the board vary, and should consult Nvidia’s Security Bulletin to ensure that they have the latest version. To download the latest drivers, users can simply head to the official website or consult the GeForce Experience application.
KitGuru Says: Keeping on top of security is always important, no matter what. It’s always best to make sure that you don’t leave your system vulnerable.
 KitGuru KitGuru.net – Tech News | Hardware News | Hardware Reviews | IOS | Mobile | Gaming | Graphics Cards
KitGuru KitGuru.net – Tech News | Hardware News | Hardware Reviews | IOS | Mobile | Gaming | Graphics Cards