Within the past year, there has been a surge of fake browser alerts pushing tech support scams, in that a prompt will appear directing users to call a number with the sole intention to rob them blind. The latest version of this seems to affect Windows-based browser, in particular Chrome, Firefox and Brave by using their APIs against them.
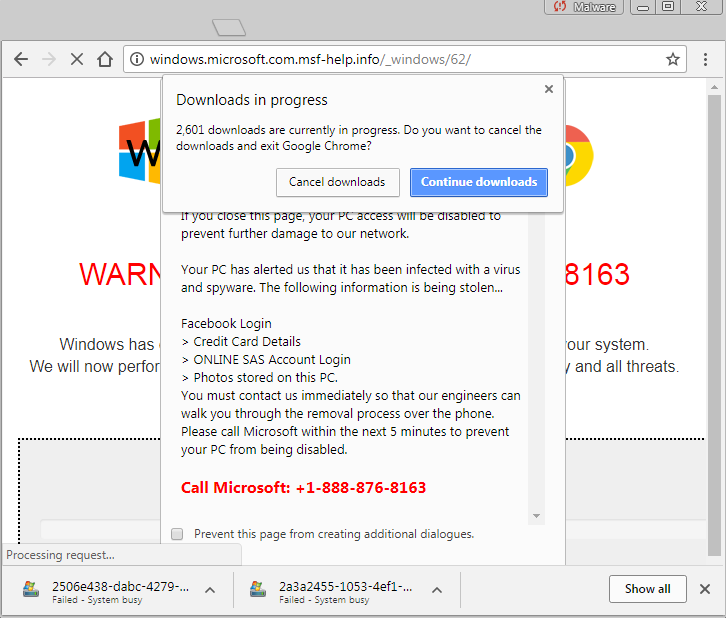
As reported by Malwarebytes, there isn’t actually any malicious code involved in the process, as attackers use the browser’s application programming interface (API) against it. The API in question prompts the browser to save directly to the disk, doing so multiple times in quick succession that it demands almost all CPU usage.
In turn, this crashes the browser in just a few seconds, with almost no time to study the effect in real-time, and prompts the misleading pop-up to appear. This alerts the user that their internet service provider (ISP) has supposedly blocked their system and they need to call Microsoft support number applied at the bottom.
Image credit: Malwarebytes
Of course, this number is fake and leads them to a scammer which will ultimately inform the unsuspecting user that they need to part with their money in order to make the problem go away. This isn’t the first time we’ve seen machines held hostage in order to retrieve money from the users and it certainly won’t be the last, but the good thing to note here is that it doesn’t target the whole system, just browsers.
Jérôme Segura, lead malware intelligence analyst at Malwarebytes stated that this targets Google Chrome users on Windows more than anything else, particularly “considering that Chrome has the most market share in the browser category,” however “other browsers will get their own landing pages, abusing other HTML APIs.”
The exploit is circumvented by the use of an ad-blocker, and those suffering can kill it via the task manager with minimal problems aside from losing their current tab selection. Unfortunately, the target market for such a scam is the less tech savvy who might not know that either of these two options exist.
Google hasn’t officially commented on the API exploit; however, a fix is expected to be in the works. It’s unlikely that Google will tread carefully in what fixes it reveals to the public and when, after a debacle last year led to Microsoft criticising the company for giving attackers an entire month to try to exploit its fix before it was made available to the public.
KitGuru Says: While I would recommend using an ad-blocker to ensure these issues are a thing of the past, don’t forget about its whitelist and potentially adding KitGuru to it. We have to survive somehow, of course. Have you ever been affected by intrusive pop-ups attempting to scam you?
 KitGuru KitGuru.net – Tech News | Hardware News | Hardware Reviews | IOS | Mobile | Gaming | Graphics Cards
KitGuru KitGuru.net – Tech News | Hardware News | Hardware Reviews | IOS | Mobile | Gaming | Graphics Cards



Why is this even news for ?
Just get me two 1080s and we call it deal okay?